-
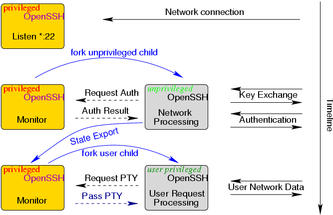
Privilege Separated OpenSSH
We use an unprivileged child process to contain and restrict the effects of programming errors. A bug in the unprivileged child process does not result in a system compromise. In other words, the goal is complete privilege separation within in OpenSSH.If the child process gets corrupted and believes that the remote user has been authenticated, access will not be granted unless the parent has reached the same decision.
Previously any corruption in the sshd could lead to an immediate remote root compromise if it happened before authentication, and to local root compromise if it happend after authentication. Privilege Separation will make such compromise very difficult if not impossible. Privilege separation is a powerful principle to improve cyber security that can also be applied to other authentication services.
Project Status
- 2002-03-18: Privilege Separated OpenSSH has been integrated into the OpenBSD cvs repository.
- 2002-03-16: User feedback has identified a few minor problems that are being fixed now.
- 2002-03-15: Finalized version. Looking for feedback.
- 2002-03-14: Minor bug fixes. Pretty stable, running on all my desktop machines.
- 2002-03-13: SSHv1 is privilege separated, too. BSD-auth is supported and other authentication systems should operate under privilege separation soon.
- 2002-03-12: All of OpenSSH is completely
privilege separated. In order to get privilege separation
after the authentication, the operating system needs to support
file descriptor passing. If no file descriptor passing is avaiable,
the privilege separation will stop after authentication was
successful.
- SSH v2 only: The privilege separation works for protocol v2 only at the moment. SSH v1 protocol is currently being worked on.
- 2002-03-11: Pre-authentication is completely privilege separated.
After authentication was successful the unprivileged child exports
its cryptographic and compression state to the privileged parent which
then proceeds.
- Cipher State: OpenSSH needs to keep track of the current IV, and for stream ciphers of the whole key state. Currently, I obtain the context from the EVP_CIPHER_CONTEXT structure.
-
Compression State Export:
I had to create two shared memory maps. Override the
allocation functions from zlib to allocate from the
first memory map. Override the allocation functions for
the first memory map to allocate entries from the second
memory map. When the process exists you have all the
control structures from the first memory map stored in
the second memory map and can use the information in the
second map to completely sync state for the first map
across processes.
This is completely transparent as the zlib library provides hooks for private allocation mechanisms.
References
-
- Preventing Privilege Escalation
- Niels Provos, Markus Friedl and Peter Honeyman, 12th USENIX Security Symposium, Washington, DC, August 2003.
- Frequently Asked Questions
Source code
The source code is available in the OpenBSD CVS respository.-
2002-03-18: You can obtain the ssh sources with the following command
cvs -d anoncvs@anoncvs1.ca.openbsd.org:/cvs get src/usr.bin/ssh
or from any other anoncvs server.
Acknowledgments
Markus Friedl has helped with writing code for privilege separation and his suggestions have improved its quality significantly.Portability
Maintaining portability is a high priority. The interface to the shared memory is very well abstracted and should be easy to re-implement on operating systems that do not support anonymous memory maps.The portable OpenSSH supports Privilege Separation. A few issues with some operating systems are still being worked on.